
RiskRecon enables clients to easily understand and act on your third-party risk by providing a rich profile of the your partner’s and supplier’s security configuration and operations.
RiskRecon enables clients to easily understand and act on your third-party risk by providing a rich profile of the your partner’s and supplier’s security configuration and operations.


RiskRecon enables clients to easily understand and act on their third-party risk through cybersecurity ratings and continuous security control assessments. They do this by providing a rich profile of the assets and details of an enterprise’s security configuration and operations.
Our asset profiles are completely refreshed every two weeks, because even if a company owned an asset a month ago, it doesn’t mean that they still do. At the heart of our asset discovery are analysts who train supervised machine learning models for each company monitored. These models enable RiskRecon to efficiently mine the internet for company systems and to ensure accurate company asset attribution as companies shift over time.
RiskRecon builds a detailed profile of every asset discovered. This asset profile provides you with an intimate understanding of how the organization has constructed their business-computing architecture.
This profile includes:
Configuring RiskRecon to match your risk appetite is simple: For each inherent risk category, simply tune a risk policy for each security criterion.
Building on RiskRecon’s unique capability to automatically risk prioritize issues, RiskRecon announced a cutting-edge capability that lets organizations automatically produce third-party cyber risk assessments and action plans that are custom-fitted to match their unique risk appetite.
In addition to automatically creating custom-fitted risk assessments and action plans, organizations can tune RiskRecon’s continuous monitoring to show only the material risk issues that violate their risk policy.
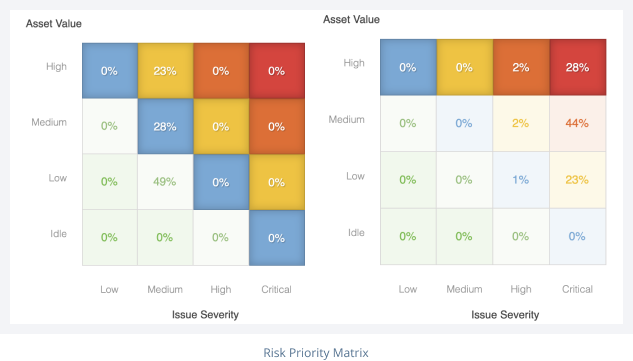
Get instant visibility of each vendor’s compliance to your custom risk policy requirements. Engaging non-performing vendors is super easy just send them the action plan that details only the issues violating your risk policy. RiskRecon automatically and continuously assesses your vendors for compliance to your risk policy, making it easy for you to understand and act on your third-party risk.
RiskRecon arms your management team with the information needed to allocate assessment resources based on risk. Instead of assessing vendors at a fixed frequency, you can adjust the assessment frequency based on vendor performance, assessing well-performing vendors less frequently than poor-performing ones.
RiskRecon’s objective assessments give you insight into which vendors are performing well and which ones are problematic. Now you can allocate more resources to those performing poorly and fewer to those that are not.

Accuracy counts when assessing the risk third and fourth parties introduce into every enterprise organization. Without it, organizations are blind to where they are vulnerable.
Reducing that risk across the ecosystem of vendors you do business with is challenging when False Positives are present – and RiskRecon proves that it is providing the highest level of accuracy possible for customers.
RiskRecon’s asset attribution is independently certified to 99.1% accuracy. And we don’t hide any of the assessment details. It’s all visible to you and your vendors at no additional fee. Action requires accuracy and transparency. RiskRecon provides you both.
Our asset profiles are completely refreshed every two weeks, because even if a company owned an asset a month ago, it doesn’t mean that they still do. At the heart of our asset discovery are analysts who train supervised machine learning models for each company monitored. These models enable RiskRecon to efficiently mine the internet for company systems and to ensure accurate company asset attribution as companies shift over time.
RiskRecon builds a detailed profile of every asset discovered. This asset profile provides you with an intimate understanding of how the organization has constructed their business-computing architecture.
This profile includes:
Configuring RiskRecon to match your risk appetite is simple: For each inherent risk category, simply tune a risk policy for each security criterion.
Building on RiskRecon’s unique capability to automatically risk prioritize issues, RiskRecon announced a cutting-edge capability that lets organizations automatically produce third-party cyber risk assessments and action plans that are custom-fitted to match their unique risk appetite.
In addition to automatically creating custom-fitted risk assessments and action plans, organizations can tune RiskRecon’s continuous monitoring to show only the material risk issues that violate their risk policy.

RiskRecon arms your management team with the information needed to allocate assessment resources based on risk. Instead of assessing vendors at a fixed frequency, you can adjust the assessment frequency based on vendor performance, assessing well-performing vendors less frequently than poor-performing ones.
RiskRecon’s objective assessments give you insight into which vendors are performing well and which ones are problematic. Now you can allocate more resources to those performing poorly and fewer to those that are not.

Accuracy counts when assessing the risk third and fourth parties introduce into every enterprise organization. Without it, organizations are blind to where they are vulnerable.
Reducing that risk across the ecosystem of vendors you do business with is challenging when False Positives are present – and RiskRecon proves that it is providing the highest level of accuracy possible for customers.
RiskRecon’s asset attribution is independently certified to 99.1% accuracy. And we don’t hide any of the assessment details. It’s all visible to you and your vendors at no additional fee. Action requires accuracy and transparency. RiskRecon provides you both.
You might be surprised at how many of your partners, suppliers and your own internet surfaces are vulnerable to cyber breaches. You might also be surprised at how few are able to identify and fix these breaches before it’s too late.
Organizations now frequently delegate their most private data and operational tasks to third parties. But as a result of these additional business relationships, an organization’s extended risk surface, where the majority of cyber threats and risk exposure tend to aggregate, expands in size and complexity.
To help safeguard your digital ecosystem from third-party risk, you need simple, real-time visibility into the cyber performance of your third-party partners. Businesses are unable to recognise and defend against potential threats without this visibility.
Of organisations use outside parties to host sensitive or important assets.
Of organisations have assets that are externally hosted that have serious or important issues or findings.
Catastrophic multi-party breach events demonstrate that supply chain layers outside of your immediate third parties can be the source of cyber risk.
Your company is vulnerable to a potential backdoor supply chain cyberattack because cybersecurity analysts are less likely to be aware of the identities of those supply chain vendors, let alone have access to audit or risk-assess them directly.
Of an organization’s assets sit on infrastructure owned by an external entity or supply chain vendor.
Organizations are 3x more likely to have severe issue findings off-prem vs. on-prem.
The internet surface area of an organisation is frequently larger and more complicated than it may appear, which makes it challenging for a third-party vendor to learn more about that organization’s cybersecurity rating and performance.
Organizations are severely disadvantaged in the event of a data breach and risk losing both current and future business relationships, vendors, or partners without a full understanding of their own risk surface.
Of organizations have internet assets/hosts in multiple countries.
Of which are spread across 10 or more countries.
Organizations now frequently delegate their most private data and operational tasks to third parties. But as a result of these additional business relationships, an organization’s extended risk surface, where the majority of cyber threats and risk exposure tend to aggregate, expands in size and complexity.
To help safeguard your digital ecosystem from third-party risk, you need simple, real-time visibility into the cyber performance of your third-party partners. Businesses are unable to recognise and defend against potential threats without this visibility.
Of organisations use outside parties to host sensitive or important assets.
Of organisations have assets that are externally hosted that have serious or important issues or findings.
Catastrophic multi-party breach events demonstrate that supply chain layers outside of your immediate third parties can be the source of cyber risk.
Your company is vulnerable to a potential backdoor supply chain cyberattack because cybersecurity analysts are less likely to be aware of the identities of those supply chain vendors, let alone have access to audit or risk-assess them directly.
Of an organization’s assets sit on infrastructure owned by an external entity or supply chain vendor.
Organizations are 3x more likely to have severe issue findings off-prem vs. on-prem.
The internet surface area of an organisation is frequently larger and more complicated than it may appear, which makes it challenging for a third-party vendor to learn more about that organization’s cybersecurity rating and performance.
Organizations are severely disadvantaged in the event of a data breach and risk losing both current and future business relationships, vendors, or partners without a full understanding of their own risk surface.
Of organizations have internet assets/hosts in multiple countries.
Of which are spread across 10 or more countries.
Contact us to book a demo with one of our KYS experts.